
Avast, an internet Security company, reports that there has been over 75,000 cases in 99 different countries (although the U.S. is not yet one of them).
At this point, most of the infections have been reported in Russia, the Ukraine, and Taiwan, but U.K. hospitals (through their National Health Service), Chinese universities, and even FedEx have reported they have infected systems.
How Does WannaCry Work?
Ransomware is a type of malicious malware that infects a computer, encrypts the data (such as documents, spreadsheets, etc.) on that computer, and displays a warning message that demands a payment to restore access (decrypt) the data. The payment is typically from $300 to $600, and is made through Bitcoin, and online digital currency that is almost impossible to trace.
Once the victim pays the ransom, they will (hopefully) be given a code to decrypt their data.
Here is what the WannyCry warning screen looks like:
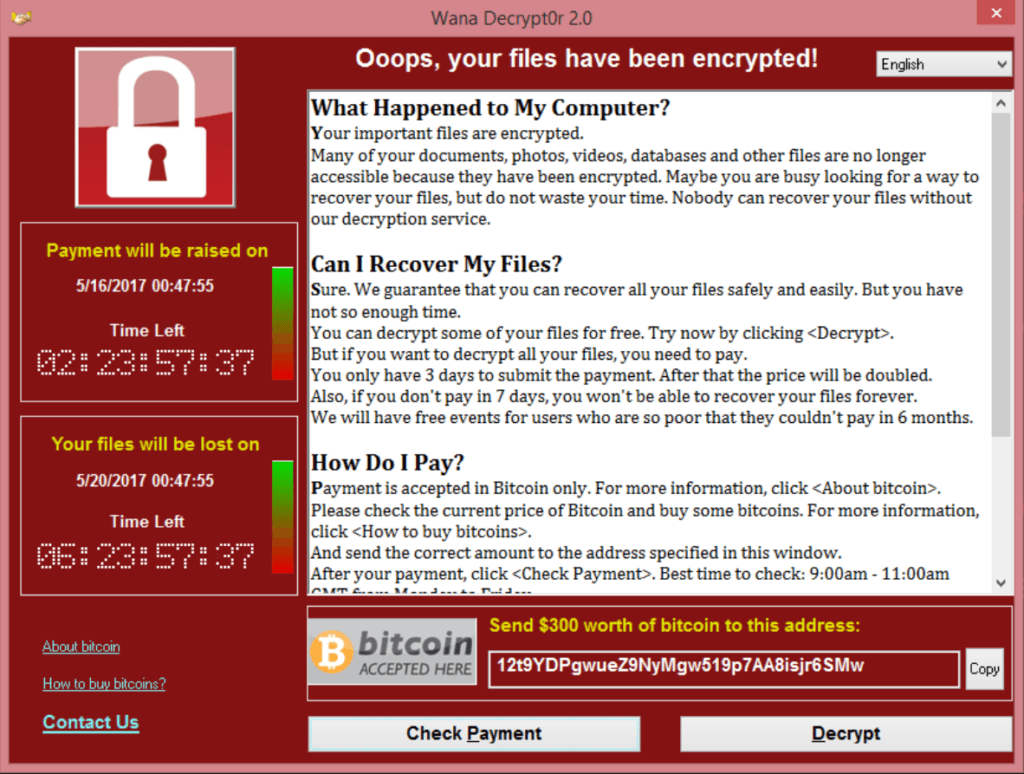
The original ransomware infection typically happens when someone opens an infected attachment that arrives with spam email, but in the case of WannaCry, the malware also had “worm” capability which allowed it to spread across networks of connected computers.
Where Did WannaCry Come From?

Although the NSA will neither confirm or deny it, they reportedly discovered the Windows vulnerability and created a hacking tool called “EternalBlue“, which allowed the NSA to break into Windows computers with that specific vulnerability.
The EternalBlue tool was allegedly part of a bigger package of tools developed by the NSA for breaking into computers, that included malware with codenames like Oddjob, Esteemaudit, and ZippyBeer.
I should note that most of the NSA tools were developed to break into pre-Windows 10 computers, especially those running the older Windows XP, but Windows 10 computers that have not been updated are also at risk.
But back to the saga…
So in March, Microsoft released a security patch for EternalBlue, and although Windows 10 computers are set to automatically install updates, there are still millions of older Windows machines in the world that are not properly updated, and never get the security patches.
A hacker group called Shadow Brokers, somehow gained access to the NSA tools, and in April leaked the EternalBlue hacking tool, which now criminal hackers have used to create the WannCry ransomware.
Whew! Certainly that’s a long, twisted tail!
How to Protect Yourself from WannaCry
Earlier this year, I published an article called “My 2017 Internet Safety Suggestions“, that included “Make Sure Your Windows Updates Are Happening“.
CLICK HERE to read the Internet Safety Suggestions article.
In the case of the WannaCry ransomware, making sure your Windows computer has the latest update is your best protection.
If you have Windows 10, your computer is already set to get the updates automatically (you have no choice). With Windows 7, it’s probably automatically set, but with that version of Windows the end-user can turn off updates.
But to double-check if updates are happening, here’s what you can do.
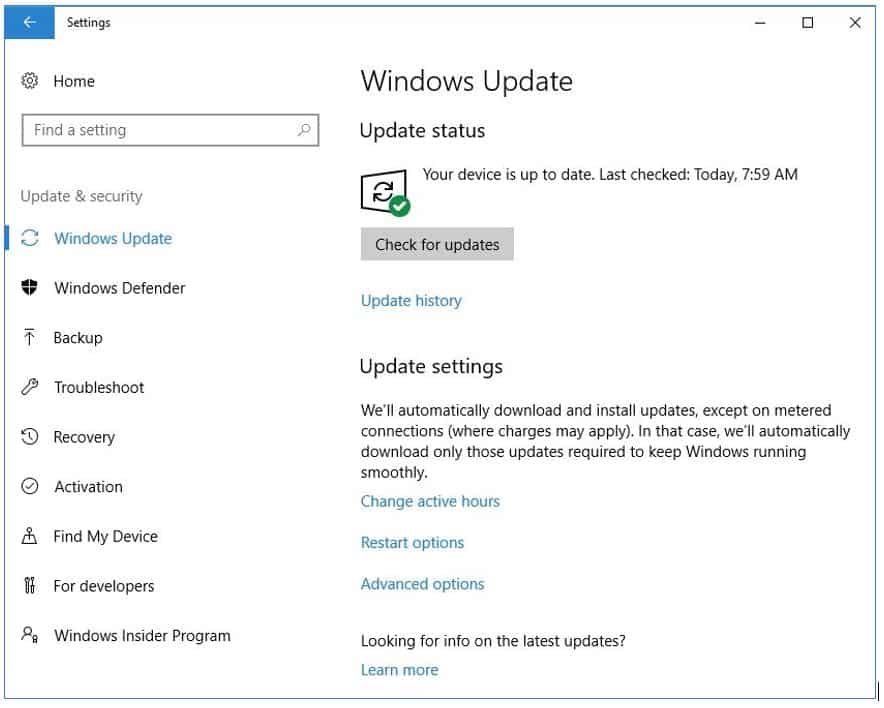
With Windows 10:
- Click the START button, choose SETTINGS, and then Update & Security
- On the left menu, click Windows Update, and notice what it says under Update Status with regards to when your computer was last updated.
- You can also click the Check For Updates button, just to make sure you have the latest update.
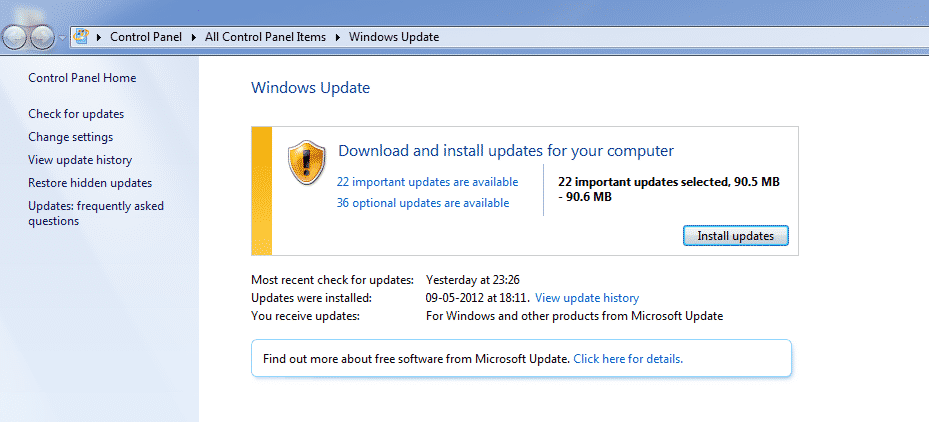
With Windows 7:
- Open the Control Panel, and click System and Security
- Choose Windows Update
- On the left menu, click Check For Updates
- On the right panel, if it says there are updates to install, click the Install Updates button
If you are using an older version of Windows (such as Windows XP or Windows Vista), Microsoft no longer provides monthly security updates for those versions (which I hate to say means it might be time to look for a new computer). However, because of the WannaCry outbreak, Microsoft added some special update patches for those version on their site. CLICK HERE to visit the Microsoft Update Catalog where you can download those Security Updates.
As always, I would love to hear any comments you have, or (sadly) hear if you’ve had any direct experience with ransomware or other types of malware! Please leave a comment below!








I followed instructions for Windows 7, found all “on” BUT have a message Windows Defender is on but out of date. Clicked update twice with no change in message. And now there is a “wannacry” icon on the screen. Can you help with new development.
Marty… do you already have an Antivirus program installed? If so, Windows Defender will probably be turned off by that program, since you don’t typically have both on (i.e. Defender is an AV and Antimalware program).
As for the WannaCry icon on the screen… Can you give me more details as to “where” it is? Is it appearing as a desktop icon? Or somewhere else?
John Lortz
I got this one. Thanks